If you want to attack your network from an external public facing IP to see what a hacker would see if they had you in their sights 🎯
Linode makes this easy, with a very negligible cost.
You can install Kali Linux in a cloud and access it via command line, or even VNC to have a full GUI.
Basically, the easiest way to do it is to set up a Linode Account = http://linode.com/
BUT I would recommend getting a free credit first with a reference, I got $100 for free with a code from Network Chuck (https://bit.ly/nc_linode). Essentially, I pay about 20 a month for my Kali Linux in the cloud.
Once you have an account, set up the Kali Linux Linode with a shared CPU – Make sure to note down the password to login through the LISH console. (remember, hackers try to compromise legitimate Linode hosts via SSH to use as excellent attack vectors that have no traceability back to them. Make sure the password is strong)
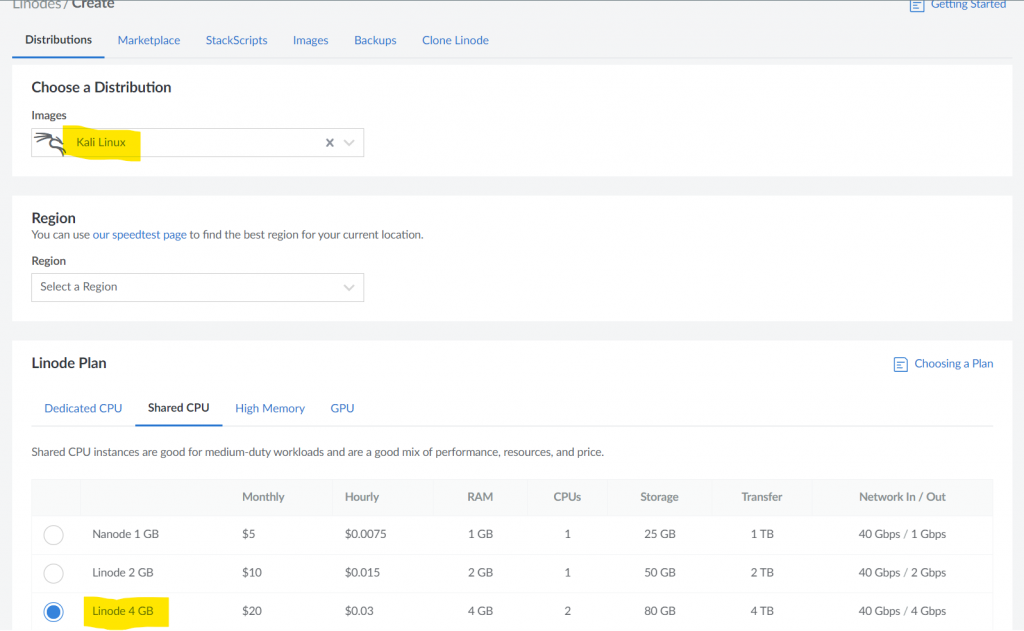
Turn it into a full VNC GUI
This part is not necessary, but say you want to ditch the command line for a GUI, it’s cool to have access to that via LINODE. To do so, it’s a few simple commands.
If you selected the VNC installation option, TigerVNC is installed. This allows you to connect remotely to the desktop environment and access Kali’s GUI tools. Perform the steps below to access your Kali Linux desktop through a VNC client. While there are many options for OS X and Windows, this guide will use RealVNC Viewer.
- From your desktop, create an SSH tunnel to your Compute Instance with the following command. Be sure to replace [username] with the VNC username you created and [ip] with the IPv4 address of your Compute Instance.
ssh -L 61000:localhost:5901 -N -l [username] [ip]- Open your preferred VNC viewer application and connect to your Compute Instance through the SSH tunnel you created. The format is
localhost:61000
- A warning may appear notifying you that the connection is unencrypted. Since you are using an SSH tunnel, your connection is encrypted over the internet. You can safely ignore this warning and continue.
- You are then prompted to enter the password you created for the VNC user.
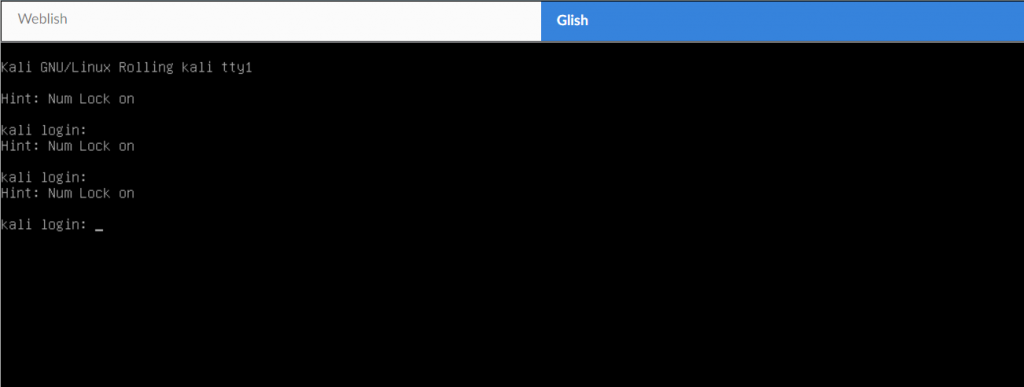
After connecting, the Kali Linux desktop should appear.
NMAP SCANNING
Once you are in, there are a few NMAP commands I like to run on my public IP whenever I make any changes that could affect the network (setting up a new nas, new firewall rule, new executable, etc).
I use the following command:
nmap -sU -A [Target IP address] (This will perform a UDP scan, and confirm the version if available, the OS, and traceroute) nmap -sS -A [Target IP address] (This will perform a stealth SYN (TCP) scan, a UDP scan, and confirm the version if available, the OS, and traceroute)
Afterwards, I like to run this command:
nmap -sX -sV [Target IP address] (xmas scan is used to trick firewalls and IDS by being more stealthily and can provide more information on the port)
if there are some ports you want to be especially mindful of:
-p [1-10000] (as an example, will scan port 1 to 10,000
The result of the scan should show all your TCP ports closed, and likely a few of your UDP ports open|filtered, this is normal for 445, 135, 137-139, and a few others. This is a result of “No response received (even after retransmissions)” The ports will likely be completely unreachable and out of grasp for any hacker to take advantage of, nothing to worry about.
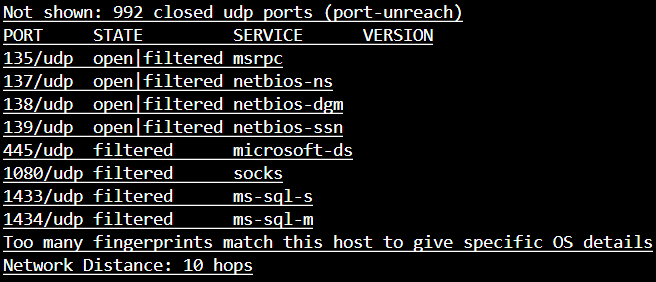
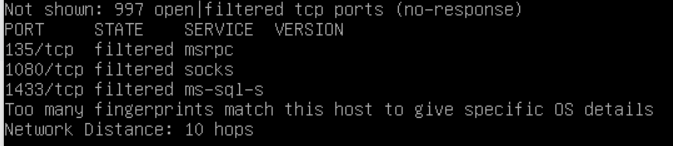
You should verify the results of any suspicious ports by using Shields UP – this will verify that the port is indeed closed or in stealth mode. It will also provide you with additional details regarding the history of the port.

Comments are closed