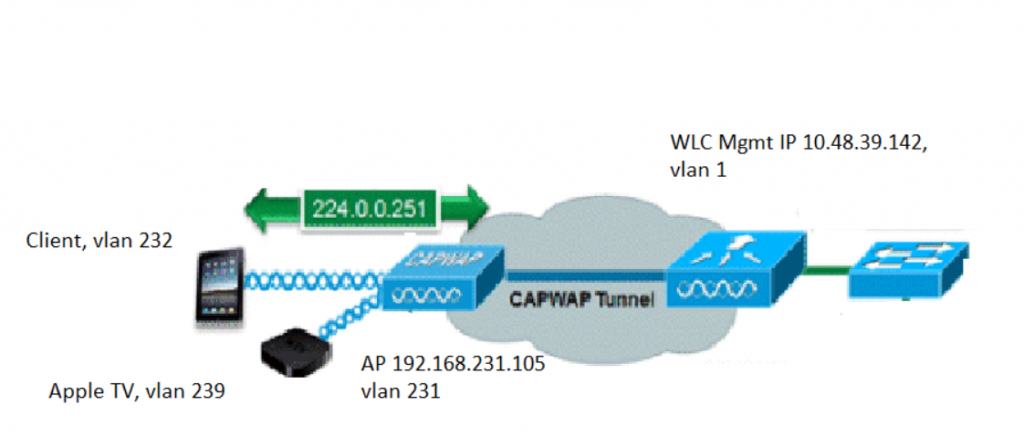
mDNS – Multicast DNS (mDNS) provides a naming service system that is easy to set up and maintain, for computers on a local link.
Difference between mDNS and DNS – Like DNS, mDNS also resolves domain names to IP addresses but was designed with Apple Bonjour services in mind. mDNS operate at local network level unlike conventional DNS which operates at global level. For example, mDNS (multicast Domain Name System) protocol can be used to search for available Chromecast on the wireless network by resolving a _googlecast_.tcp.local service name when making an mDNS broadcast.
mDNS protocol operates on service announcements and service queries which allow devices to ask and advertise specific applications such as:
- Printing Services
- File Sharing Services
- Remote Desktop Services
- iTunes File Sharing
- iTunes Wireless iDevice Syncing (in Apple iOS v5.0+)
Each query or advertisement is sent to the mDNS multicast address for delivery to all clients on the subnet. It relies on mDNS operating at UDP port 5353 and each query or advertisement is sent to the following reserved group addresses:
The addresses used by the mDNS protocol are link-local multicast addresses and thus are only forwarded on the local L2 domain. Routers cannot use multicast routing to redirect the traffic because the time to live (TTL) is set to one, and link-local multicast is meant to stay local by design. However, mDNS repeaters have been developed to forward mDNS traffic between VLANs or subnets.
DYNAMIC DNS- This allows assigning a fixed domain name to a dynamic WAN IP address of your gateway, which enables the Internet hosts to access the device or the hosts in LAN using the domain names.
To simplify, your ISP will likely change your IP ever so often, once a month or so. If you have a website domain name that is linked to your public IP, you need it to be dynamically associated so that when your IP changes your host name will still be reachable.
DDNS is usually offered by the DDNS provider such as DynDNS, No-IP, Peanuthull and Comexe. DDNS providers offer users the DDNS client.
UPnP– (Universal Plug and Play) is the networking protocol that allows devices to discover each other and then establish connections for communication. For security concerns, typically we don’t want to have this on any network that is considered a secure network.
UPnP uses common Internet technologies. It assumes the network must run Internet Protocol (IP) and then uses HTTP, SOAP and XML on top of IP, in order to provide device/service description, actions, data transfer and eventing. Device search requests and advertisements are supported by running HTTP on top of UDP using multicast (known as HTTPMU). Responses to search requests are also sent over UDP, but are instead sent using unicast (known as HTTPU). UPnP uses UDP due to its lower overhead in not requiring confirmation of received data and retransmission of corrupt packets.
UPnP uses UDP port 1900 and all used TCP ports are derived from the SSDP alive and response messages. One device infected with malware can infect all other devices it connects with, this is why I recommend DISABLING UPnP on the GATEWAY/ROUTER
IGMP- The Internet Group Management Protocol (IGMP) is a protocol that allows several devices to share one IP address so they can all receive the same data. IGMP is a network layer protocol used to set up multicasting on networks that use the Internet Protocol version 4 (IPv4). Specifically, IGMP allows devices to join a multicasting group.
Applications:
- Streaming – Multicast routing protocol are used for audio and video streaming over the network i.e., either one-to-many or many-to-many.
- Gaming – Internet group management protocol is often used in simulation games which has multiple users over the network such as online games.
- Web Conferencing tools – Video conferencing is a new method to meet people from your own convenience and IGMP connects to the users for conferencing and transfers the message/data packets efficiently.
IPTV- Unlike downloaded media, IPTV offers the ability to stream the source media continuously. As a result, a client media player can begin playing the content (such as a TV channel) almost immediately. This is known as streaming media. The security risk here is to ensure that the software you are using does not have any known vulns such as WebTV Player, (CVE-2020-9380). Make sure it’s patched, up to date, and keep an eye out.
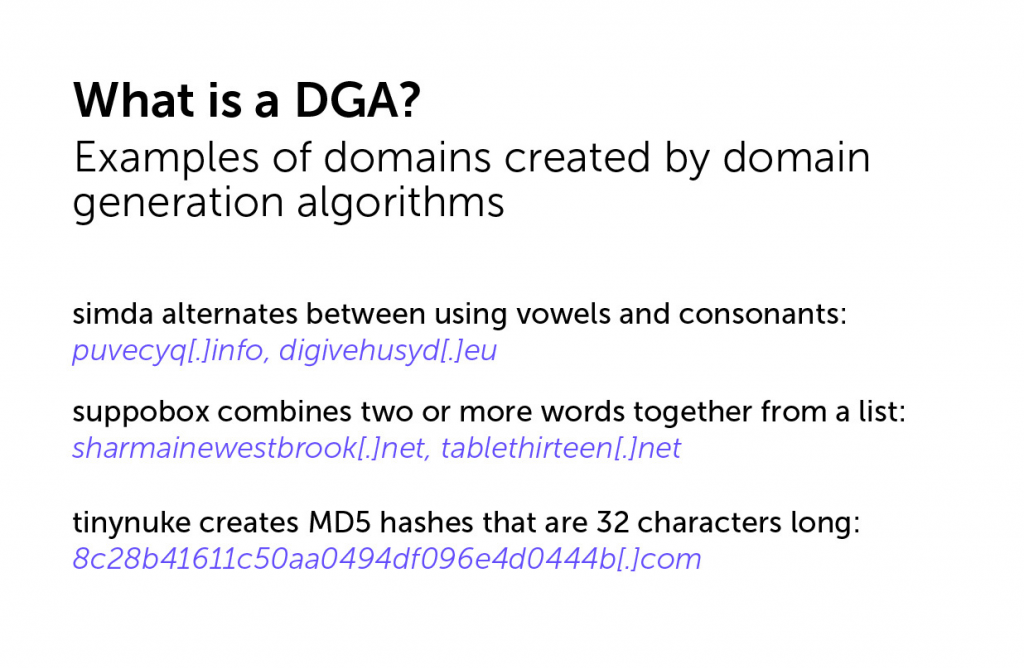
DGA- DGAs generate domains over time that are used as rendezvous points where the infected hosts and the C&C server connect to keep the scheme going. At predetermined intervals, the DGA generates new names for its C&C server using one of several techniques.
It may create what looks like a randomly generated set of numbers or letters (actually, like so-called random number generators, they start with a random seed value) and tack on a top-level domain suffix (e.g., .com or .org). Similarly, pseudo-random number generators produce sequences of numbers that appear like they are random.
These domains are launched systematically and follow patterns that the malware or botnet understands. Bad actors can also configure the DGA to register a new domain at whatever frequency is useful to them—every day, hour, or even minute.
WS discovery (Discovery, Transfer)- Is a protocol that is meant for LAN, but once exposed to the internet can cause major DdoS attack vectors. A multicast discovery protocol to locate services on a local network. It operates over TCP and UDP port 3702 and uses IP multicast address 239.255.255.250 or FF02::C. For example, it can allow users to access the SMB service on Synology NAS via Windows network discovery. In order words, you can see which shares are available right through the file explorer.
DNS Sinkhole- DNS sinkhole or black hole DNS is used to spoof DNS servers to prevent resolving hostnames of specified URLs. This can be achieved by configuring the DNS forwarder to return a false IP address to a specific URL. DNS sinkholing can be used to prevent access to malicious URLs at an enterprise level. The malicious URLs can be blocked by adding a false entry in the DNS and thus there will be a second level of protection. Normally firewalls and proxies are used to block malicious traffic across the organization.
A DNS sinkhole has a major set of functionalities that has multiple use cases:
- Blocking drive-by downloads
DNS sinkhole redirects user access to a legitimate website that an attacker has secretly inserted with a malicious hidden link, which forces the client to download and execute malicious code without their knowledge.
- Blocking C&C channels
DNSSEC- DNSSEC creates a secure domain name system by adding cryptographic signatures to existing DNS records. These digital signatures are stored in DNS name servers alongside common record types like A, AAAA, MX, CNAME, etc. By checking its associated signature, you can verify that a requested DNS record comes from its authoritative name server and wasn’t altered en-route, opposed to a fake record injected in a man-in-the-middle attack.
To facilitate signature validation, DNSSEC adds a few new DNS record types:
- RRSIG – Contains a cryptographic signature
- DNSKEY – Contains a public signing key
- DS – Contains the hash of a DNSKEY record
- NSEC and NSEC3 – For explicit denial-of-existence of a DNS record
- CDNSKEY and CDS – For a child zone requesting updates to DS record(s) in the parent zone
LSASS.EXE- Local Security Authority Subsystem Service is a process in Microsoft Windows operating systems that is responsible for enforcing the security policy on the system. It verifies users logging on to a Windows computer or server, handles password changes, and creates access tokens. It also writes to the Windows Security Log.
SAM- The Security Account Manager is a database file in Windows that stores users’ passwords. It can be used to authenticate local and remote users. Beginning with Windows 2000 SP4, Active Directory authenticates remote users. SAM uses cryptographic measures to prevent unauthenticated users accessing the system.
The user passwords are stored in a hashed format in a registry hive either as an LM hash or as an NTLM hash. This file can be found in %SystemRoot%/system32/config/SAM and is mounted on HKLM/SAM and SYSTEM privileges are required to view it.
Active Directory- Active Directory is a database that stores and organizes enterprise resources as objects. You can think of Active Directory as a database that stores users and device configurations. Active directory is the service used that is served by the domain controller.
Domain Controller- A domain controller, is simply a server running Active Directory (or other authenticating service) that authenticates users and devices. The domain controller serves the service which is typically active directory or other identity management systems.
Kerberos-Windows default authentication protocol, used in Active Directory. Even in untrusted networks. It is used for authenticating hosts. Plain test passwords should never be sent.
Kernel- kernel refers to the core component of an operating system. It acts as a bridge between applications and the hardware of a computer system, managing system resources, providing essential services, and enabling communication between software and hardware components.
Here are a few practical examples of what the kernel does and how it functions in relation to cybersecurity:
- Memory Management: The kernel is responsible for managing the memory resources of the system, allocating memory to processes and ensuring their isolation. It enforces memory protection mechanisms to prevent unauthorized access or tampering, protecting the integrity of sensitive data and preventing attacks like buffer overflows.
- Process Management: The kernel manages the execution of processes and threads in the system. It enforces process isolation and privilege separation, ensuring that each process operates within its defined boundaries and preventing unauthorized access to system resources.
- Device Drivers and I/O: The kernel provides device drivers to interface with hardware devices. It controls input/output operations and enforces access control policies to prevent unauthorized access or manipulation of devices. By managing device communication, the kernel helps protect against attacks that exploit vulnerable drivers or attempt to interfere with system devices.
Hive Registry- The Hive Registry is implemented as a collection of files on the Windows file system. It consists of several “hives” that store different types of information, such as the HKEY_LOCAL_MACHINE hive for system-wide settings and the HKEY_CURRENT_USER hive for individual user settings. The registry is structured as a hierarchical database, with keys representing folders and values storing specific data.
Here are a few practical examples of what the Hive Registry does and how it functions:
- System Configuration: The Hive Registry stores system configuration settings, including hardware configurations, device drivers, startup programs, network settings, and security-related parameters. It provides a centralized location for managing and retrieving system-level configuration information.
- User Profiles and Preferences: Each user account in Windows has its own registry hive that stores individual user preferences, settings, application configurations, and user-specific data. This includes information such as desktop preferences, application settings, browser history, and user-specific security settings. The Hive Registry ensures that these user-specific configurations are maintained and accessible for each user.
- Security Policies: The Hive Registry includes security-related information and policies that control access permissions, user privileges, audit settings, and other security configurations. These settings define access controls, password policies, firewall rules, and other security measures enforced by the operating system.

Comments are closed