Security is a culture that needs to be embedded into any simple or complex framework when technology is involved.
A NAS can be an incredibly fruitful objective for a malicious hacker to exploit. A simple user or business user will of course enjoy different levels of convenience. The natural trade-off when it comes to security is the amount of convenience the user is willing to loose. I think optimal security is best achieved with a common-sense approach if you comprehend the risks correctly.
The first step (already done with Synology DSM) is to deactivate the default admin/guest and create a new admin account with a different username string. (ex: p-danadmin (power account))
For password, I highly recommend reviewing my blog on password managers and why they are very crucial nowadays. Set up a long long 25+ character (with symbols, numbers, etc) password with 2FA. I recommend 25+ because nothing is going to crack it, and if you use a password manager, why not?

The new admin account is separated from the account I actually use to share files and folders, obviously this admin account is ONLY for administrations purposes.
In the Control Panel, there are a few obvious settings that should be enabled to protect your data.
The first step is to enable lengthy password requirements with 2FA mandatory. The next logical step is to enable “Auto-block” I like my setting to run as 3 password fails within 5 minutes get a 1 day block… I like to have some leeway with human error if you ever have to manually type in a password, and also I like to invite anybody to crack a 25 length password with these controls. (If I got a log alert of many IPs being blocked, then I may increase the auto-block measure, so far, I had 0 failed attempts from malicious actors.). In the same page, enable DOS protection.
After this step is complete, I recommend disabling any services [applications] that you DO NOT need. For example, all terminal services are closed for me. Secondly, I only use SMB for file transfer, all other protocols in file services are disabled except SFTP for the one-off. After installing your necessary packages, recommend reviewing the default application privileges for users, as such:
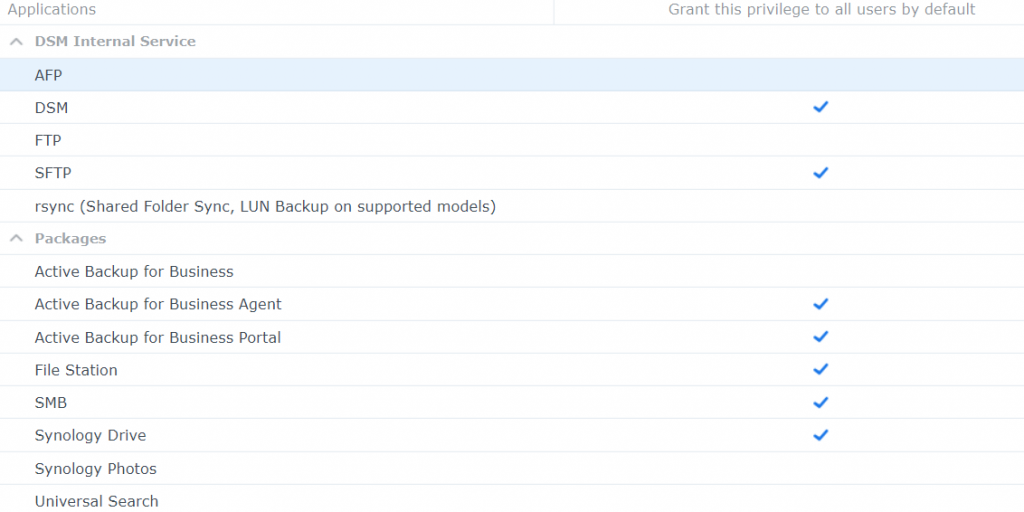
Change the default ports to something like 6750 for Management UI. Once this step is done, you can decide on External Access to your NAS. Now, the best route possible would be to VPN into your network when you need access. Personally, I believe Quick Connect is a safe way to externally access your NAS, read the WHITE PAPERS, and understand that no ports will be opened from the internet via port forwarding to your NAS.
However, if you have the option to set up DDNS for dynamic IPs handed by your ISP, and you want to use your NAS (or better yet, a gateway firewall) as a VPN, this is preferred.
Finally, I would begin setting up users that would use the NAS for data storage here. Typically, the password requirements would be the same for me as for these users. Carefully monitor application privileges and permissions for these users. If malware infects a user and gets into the NAS hard-drive, it should stay locally within that users privilege level. Especially since Malware has a hard time understanding NAS DSM operating system, unless crafted specifically for the purpose.
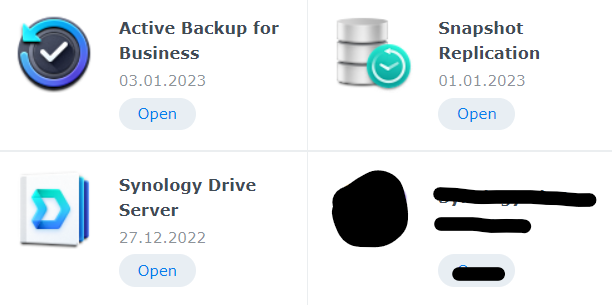
My recommendation here is to set up snapshot replication (for total restoration of a file share), windows active backup for business (to restore an entire PC..server…virtual machine), and Synology drive (for file versioning). MAKE SURE TO UPDATE OFTEN FOR ANY PATCHES, THIS IS THE KEY TO SECURITY.
Next is the firewall, I went back and forth whether I want to use NAS ram for a firewall, because I already hosted a docker container on it. After running recon using Kali on my NAS, it had open ports (UPnP, as an example) that even if the service was not running, I wanted to be closed. Defense in depth.. would like to screenshot what my settings are.
ONLY thing you have to read, is that the ALLOW rules go first for MANAGEMENT UI, then set up your final DENY rule last. Make sure you don’t lock yourself out.
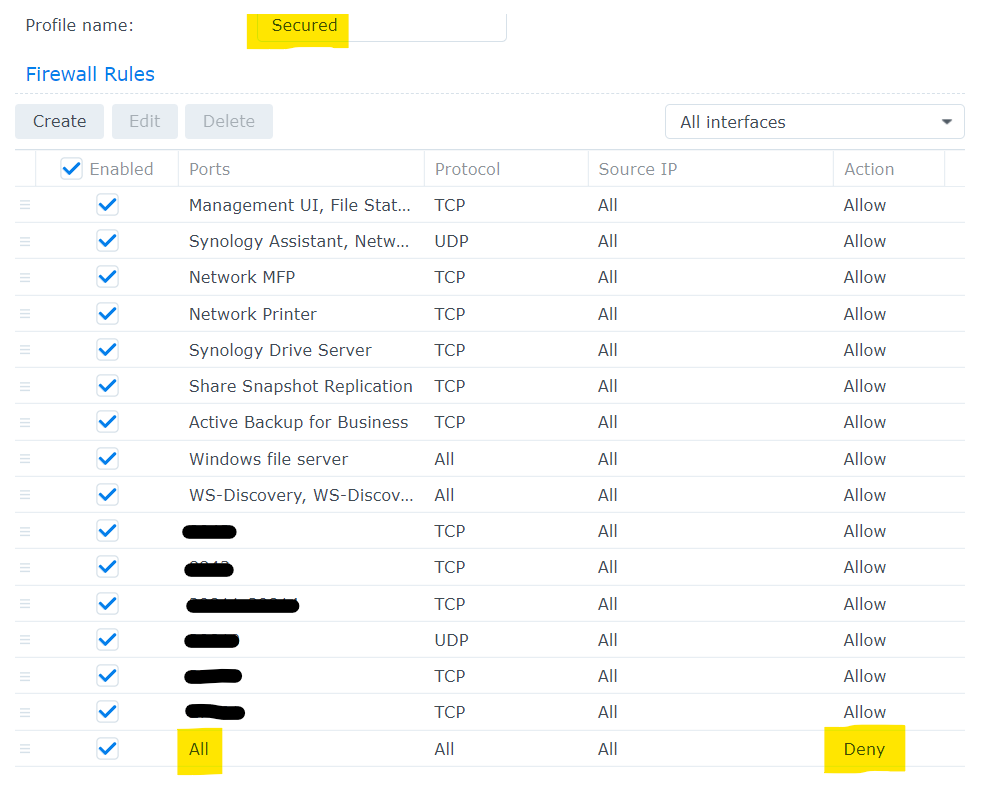
All of this should keep your NAS config safe. Remember, security is the enemy of convenience, so decide what you are able to risk loosing.
Finally, you may what you will do if a SMB shared user had a compromise on their machine which transferred a virus or ransomware to the NAS. As long as the permission is localized to the user, with snapshot replication, things should be good. Take a look at the following video for some great information on what to do:

Comments are closed